
Prepared for the GDPR?
Discover how the new General Data Protection Regulation (GDPR) sharpens data protection requirements. And how it increases the responsibility you have due to working with consumption reading.
What is it about and who is responsible?
As of May 2018, when the new GDPR took effect, you must to a greater extent consider how you collect, protect and handle your tenants’ data. In other words, you must be able to document the security level in your metering solutions and how you and your solution provider handle data security.
According to the GDPR, data protection and security must be implemented in a metering solution from the start. This makes it tempting to believe that your solution provider is responsible for data security. And he is – too – but since you work with consumption reading, you are responsible for ensuring that your solutions comply with the GDPR. Therefore, you must know what to ask your solutions provider to ensure your operation and what to answer if tenants have questions about their data protection rights.
What Kamstrup does
To make sure that our metering solutions can always deliver data that are both confidential and in their original form, we develop and design them with the following security principles in mind:
Data Encryption
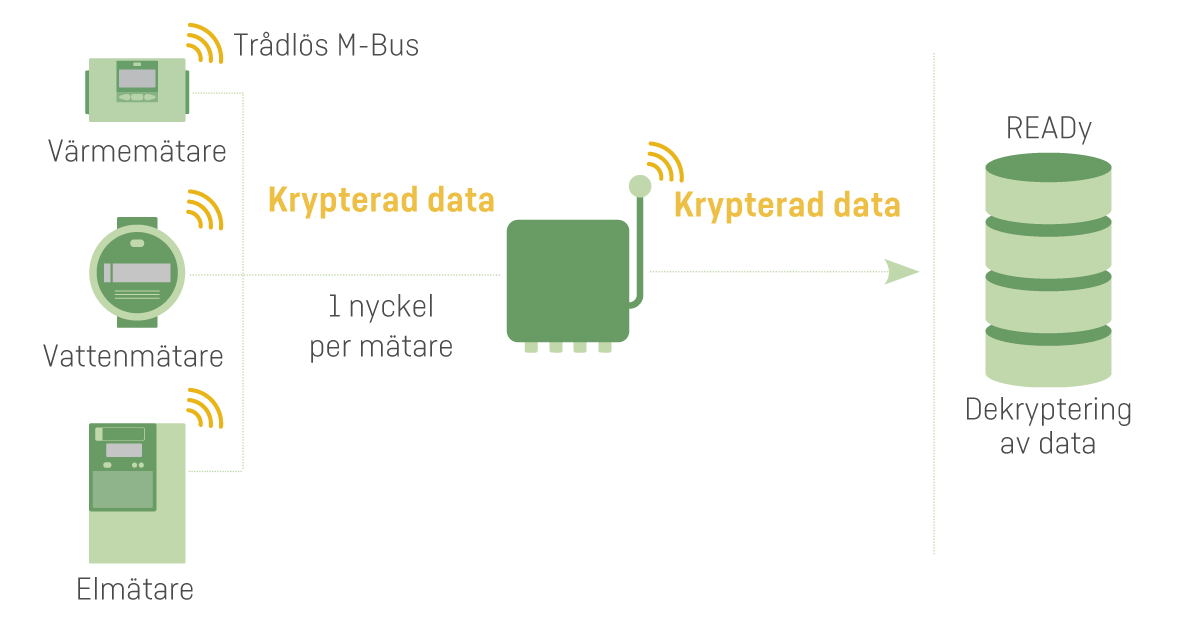
All metering devices have individual encryption keys to protect data from meter to collection unit and to the server. Data storage and decryption happen solely behind firewalls etc., where the rest of the chain is also protected.
Below, you see how we protect data throughout the chain. This varies from solution provider to solution provider. Some use a shared encryption key from meter to collection unit, others decrypt data before they reach the server.
Role-based access to data
Data security is not only a technical matter. It is also about internal processes.
Among other things, this means that there is a difference between who needs to see and handle which data and when to do so. Because of this, our solutions make it easy to handle roles and rights and perform the restrictions required to ensure your compliance to the GDPR.
Logging of Acitvity
An important element of data security is the human factor – because no chain is stronger than its weakest link. This is why activity logs and traceability in our solutions ensure full transparency, so that you know exactly which user has done what and at what time. In this way, you can always live up to your documentation responsibility in case of a security breach or suspicion of this.
Multiple Security Layers
We consider security in every step from architecture and design to development and operation. Therefore, our solutions have several layers of functions and controls to ensure that you can live up to the responsibility you have for the data of your tenants. Thanks to this, a potential security breach will be isolated to a single part of the system and the damage will be limited.
Contingency Plan
If a security breach does happen, we have a solid plan for how we – and you – are quickly up and running again. This involves a number of clear steps for how we detect a security breach, clarify its scale and contact the people who may be affected. In that way, you can rest assured that we are always prepared.
A shared responsibility
As part of working with consumption reading, you are responsible for collecting, protecting and handling your tenants’ data. Therefore, it is key that you know how your metering solutions are set up and secured. This only happens by asking questions to your solutions provider and insisting on transparency.
As a solution provider, we are responsible for the solutions we develop, operate and host for many customers worldwide. So, transparency is medication we gladly take ourselves. A Kamstrup solution is secure. We vouch for that.

Questions you should ask your solutions provider
- How do I explain to tenants how their meter data is protected?
- How do you handle individual encryption and encryption keys?
- Can you document the security of your solutions?
- Can you document how you continuously work with data security?
- How do you manage system rights and log who is doing and when?





